The docker-compose tool is pretty popular for running dockerized applications in a local development environment. All we need to do is write a Compose file containing the configuration for the application’s services and have a running Docker engine for deployment. From here, we can get the application running locally in a few seconds with a single `docker-compose up` command. If all is working as it should, you should be able to see that wslhost is bound to the local loopback on port 2375, and that envoy.exe is bound to “IPv4 unspecified” on 2375 as well: Now I was finally able to use a computer with some significant hardware as my Docker host. Unit Description=Docker Socket for the API Socket ListenStream=2375 BindIPv6Only=both Service=docker.service Install WantedBy=sockets.target Then enable this new socket: systemctl enable docker-tcp.socket systemctl enable docker.socket systemctl stop docker systemctl start docker-tcp.socket systemctl start docker. Test that it's working. Port 2375, one of the two ports Docker API uses, is for unencrypted and unauthenticated communication. There is, however, a notable difference between the two malware variants’ method of attack. While the XORDDoS attack infiltrated the Docker server to infect all the containers hosted on it, the Kaiji attack deploys its own container that.
- Docker Tcp Port 2375
- Docker Port 2375 Connection Refused
- Docker Port 2375 Security
- Docker Open Port 2375
The Docker Engine and client aren't included with Windows and need to be installed and configured individually. Furthermore, the Docker Engine can accept many custom configurations. Some examples include configuring how the daemon accepts incoming requests, default networking options, and debug/log settings. On Windows, these configurations can be specified in a configuration file or by using Windows Service control manager. This document details how to install and configure the Docker Engine, and also provides some examples of commonly used configurations.
Install Docker
You need Docker in order to work with Windows Containers. Docker consists of the Docker Engine (dockerd.exe), and the Docker client (docker.exe). The easiest way to get everything installed is in the quickstart guide, which will help you get everything set up and run your first container.
Docker Tcp Port 2375
For scripted installations, see Use a script to install Docker EE.
Before you can use Docker, you'll need to install the container images. For more information, see docs for our container base images.
Configure Docker with a configuration file
The preferred method for configuring the Docker Engine on Windows is using a configuration file. The configuration file can be found at 'C:ProgramDataDockerconfigdaemon.json'. You can create this file if it doesn't already exist.
Note
Not every available Docker configuration option applies to Docker on Windows. The following example shows the configuration options that do apply. For more information about Docker Engine configuration, see Docker daemon configuration file.
You only need to add the desired configuration changes to the configuration file. For example, the following sample configures the Docker Engine to accept incoming connections on port 2375. All other configuration options will use default values.
Likewise, the following sample configures the Docker daemon to keep images and containers in an alternate path. If not specified, thedefault is c:programdatadocker.
The following sample configures the Docker daemon to only accept secured connections over port 2376.
Configure Docker on the Docker service
The Docker Engine can also be configured by modifying the Docker service with sc config. Using this method, Docker Engine flags are set directly on the Docker service. Run the following command in a command prompt (cmd.exe not PowerShell):
Note
You don't need to run this command if your daemon.json file already contains the 'hosts': ['tcp://0.0.0.0:2375'] entry.
Common configuration
The following configuration file examples show common Docker configurations. These can be combined into a single configuration file.
Default network creation
To configure the Docker Engine so that it doesn't create a default NAT network, use the following configuration.
For more information, see Manage Docker Networks.
Set Docker security group
When you've signed in to the Docker host and are locally running Docker commands, these commands are run through a named pipe. By default, only members of the Administrators group can access the Docker Engine through the named pipe. To specify a security group that has this access, use the group flag.
Proxy configuration
To set proxy information for docker search and docker pull, create a Windows environment variable with the name HTTP_PROXY or HTTPS_PROXY, and a value of the proxy information. This can be completed with PowerShell using a command similar to this:
Once the variable has been set, restart the Docker service.
For more information, see Windows Configuration File on Docker.com.
How to uninstall Docker
This section will tell you how to uninstall Docker and perform a full cleanup of Docker system components from your Windows 10 or Windows Server 2016 system.
Note
Docker Port 2375 Connection Refused
You must run all commands in these instructions from an elevated PowerShell session.
Prepare your system for Docker's removal
Before you uninstall Docker, make sure no containers are running on your system.
Run the following cmdlets to check for running containers:
It's also good practice to remove all containers, container images, networks, and volumes from your system before removing Docker. You can do this by running the following cmdlet:
Uninstall Docker
Next, you'll need to actually uninstall Docker.
To uninstall Docker on Windows 10
- Go to Settings > Apps on your Windows 10 machine
- Under Apps & Features, find Docker for Windows
- Go to Docker for Windows > Uninstall
To uninstall Docker on Windows Server 2016:
From an elevated PowerShell session, use the Uninstall-Package and Uninstall-Module cmdlets to remove the Docker module and its corresponding Package Management Provider from your system, as shown in the following example:
Tip
You can find the Package Provider that you used to install Docker with PS C:> Get-PackageProvider -Name *Docker*
Clean up Docker data and system components
After you uninstall Docker, you'll need to remove Docker's default networks so their configuration won't remain on your system after Docker is gone. You can do this by running the following cmdlet:
To remove Docker's default networks on Windows Server 2016.
Run the following cmdlet to remove Docker's program data from your system:
You may also want to remove the Windows optional features associated with Docker/containers on Windows.
This includes the 'Containers' feature, which is automatically enabled on any Windows 10 or Windows Server 2016 when Docker is installed. It may also include the 'Hyper-V' feature, which is automatically enabled on Windows 10 when Docker is installed, but must be explicitly enabled on Windows Server 2016.
Important
The Hyper-V feature is a general virtualization feature that enables much more than just containers. Before disabling the Hyper-V feature, make sure there are no other virtualized components on your system that require Hyper-V.
To remove Windows features on Windows 10:
- Go to Control Panel > Programs > Programs and Features > Turn Windows features on or off.
- Find the name of the feature or features you want to disable—in this case, Containers and (optionally) Hyper-V.
- Uncheck the box next to the name of the feature you want to disable.
- Select 'OK'
To remove Windows features on Windows Server 2016:
From an elevated PowerShell session, run the following cmdlets to disable the Containers and (optionally) Hyper-V features from your system:
Reboot your system
To finish uninstallation and cleanup, run the following cmdlet from an elevated PowerShell session to reboot your system:
As you know, docking services are booming, docking container attacks are also on the rise. But this post will illustrate how the intruder is trying to compromise the docker API due to a weak setup.
Docker Port 2375 Security
Table of Content
- Docker architecture
- Enable Docker API for Remote connection
- Abusing Docker API
Docker Architecture
Docker uses a client-server architecture, the main components of the docker are docker-daemon, docker-CLI and API.
Docker Daemon: Use manage docker object such as network, volume, docker image & container.
Docker CLI: A command-line interface used to execute the command to pull, run and build the docker image.
Docker API: It is a kind of interface used between Daemon and CLI to communicate with each other through Unix or tcp socket.
As we know the usage of docker service in any organisation at their boom because it has reduced efforts of the developer in the host in the application within their infrastructure. When you install docker on a host machine, the daemon and CLI communicate with each other through Unix Socket that represents a loopback address. If you want to access the docker application externally, then bind the API over a TCP port.
The time you allow the docker API to be accessed over TCP connection through ports such as 2375, 2376, 2377 that means a docker CLI which is running outside the host machine will be able to access the docker daemon remotely.
The attacker always checks for such type of port using Shodan, they try to connect with docker remotely in order to exploit the docker daemon. Their several dockers application listening over port 2375 for remote connection.
Enable Docker API for Remote connection
Initially, you can observe that the target host does not have any port open for docker service when we used nmap port scan for 192.168.0.156 which is the IP of the host machine where docker application is running.
At host machine, we try to identify a process for docker, as we have mentioned above by default it runs over Unix sockets.
Now modify the configuration for REST API in order to access the docker daemon externally.
Make the changes as a highlight in the image with the help of following commands.
Now, if you will explore the docker process, you will notice the change.
Abusing Docker API
Now attacker always looks for such network IP where docker is accessible through API over 2375/tcp port in order to establish a remote connection with the docker application. As you can see, we try to scan the host machine to identify open port for docker API using nmap port scan.
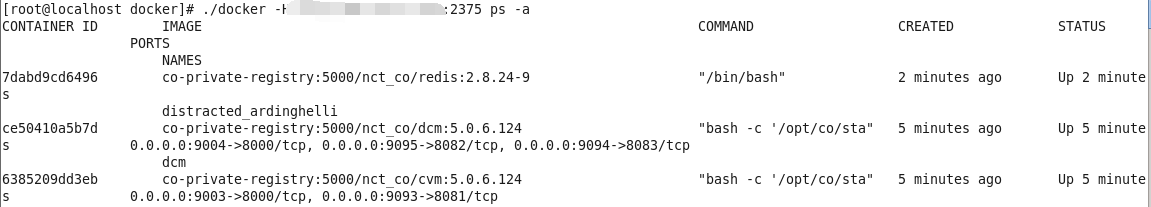
Once the port is open and accessible, you can try to connect with docker daemon on the target machine. But for this, you need to install a docker on your local machine too. So, we have installed docker on Kali Linux as well as we docker running on our target machine too. Now to ensure that we can access docker daemon remotely, we execute the following command to identify the installed docker version.
Syntax: docker -H <remote host ip> :<port> <docker-command>
Further, we try to enumerate the docker images running on the remote machine
Similarly, we try to identify the process for running a container with the help of the following command, so that we can try to access the container remotely.
Docker Open Port 2375
Thus, in this way, the weak configured API which is exposed for external connection can be abused an attack. This could result in container hijacking or an attacker can hide the persistence threat for reverse connection. Also, if the installed version of docker is exploitable against container escape attack, then, the attack can easily compromise the whole host machine and try to obtain the root access of the main machine (host).
Author: Geet Madan is a Certified Ethical Hacker, Researcher and Technical Writer at Hacking Articles on Information Security. Contact here